In my original WEP cracker article, I walked you through a WEP crack using the airodump-ng tool, the aireplay-ng tool, and the aircrack utility. I used aircrack to crack my WEP key.
The other two tools, aireplay and airodump I used to sniff the wireless traffic and then inject packets into the wireless stream in order to speed up my WEP crack. These three tools provide very deep levels of control.
You can modify the TCP traffic to, for instance, inject a certain number of packets during a specific period of time. You can really fine tune your attack with aireplay. Aircrack also provides a huge list of options when attacking a password.
This level of granularity and control can really help you when you are out on wireless security audits. However, I’m going to discuss the Fern WiFi Cracker with you. It’s a pretty nifty utility, and you can use Fern to automate a WiFi crack with just a few mouse clicks.
Automation Using the Fern WiFi Cracker
Just so you know, I still prefer and recommend you study the other methods to crack WEP as well, by using airodump, aireplay, and aircrack.
Why? Because in order to be a good network security professional, you need to KNOW how this stuff works. It’s not enough to be able to click a few buttons. We call those people keyboard jockies or tool monkeys.) Understand what’s going on under the surface. WiFi hacking software comes and goes, but aircrack, airodump, and aireplay have been around for a long time. They’re all quality products and you should know how each of these three tools works and how they can be used in conjunction with one another for a successful WiFi crack. The Fern WiFi cracker is an example of some fairly new WiFi hacking software that’s worth it.
Fern is a great WiFi cracker to use in a pinch and it’s already included in Back Track and Kali Linux. However, you can download Fern’s source code right here. We can use Fern to do a WiFi crack against a WEP encrypted network. Start by launching Fern from the Applications menu button at the top-left corner of the screen.
If you’re running Kali Linux:
Applications > Kali Linux > Wireless Attacks > Wireless Tools
If you’re running Back Track:
Applications > Back Track > Exploitation Tools > Wireless Exploitation Tools >WLAN Exploitation
Launch the Fern WiFi Cracker and Crack WEP
From the menu, click Fern-wifi-cracker to launch the tool.
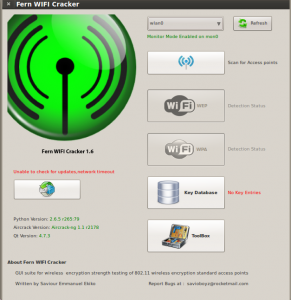
You should already have your wireless card in monitor mode. If not see my previous article right now.
Click the drop down menu at the top of Fern and select your wireless adapter from this list. Click OK to any message boxes you get. After a few moments, the message Monitor Mode Enabled on… should appear in green as seen in the image.
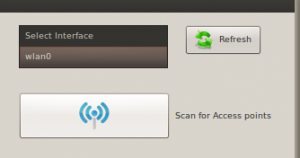
Then click Scan for Access Points.
Fern will scan for WiFi networks in range, and will begin populating the WEP and WPA boxes.

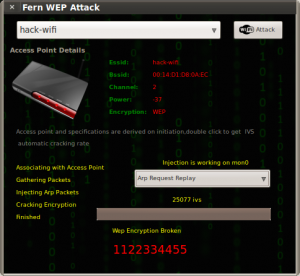
Once the the Fern WiFi Cracker finishes scanning for networks, you can select the network you are targeting by finding it in either the WEP section or the WPA section. In this example, I am targeting a WEP encrypted network with an SSID of Hack-WiFi.
You will have to select your target network from the drop down box and then clicking the WiFi Attack button to the right.
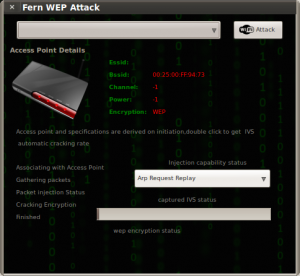

The Fern WiFi Cracker will now begin an automated WEP crack against the hack-wifi network. This may take some time, so if you need to get some coffee or take a dump, go for it. You’ll have a Please Wait… screen for a long time, as Fern goes through the process.
Remember, Fern is completely automated WiFi hacking software, so there isn’t anything left to do at this point than to just allow Fern to sniff the WiFi network, authenticate to the device, begin injecting replay traffic, and finally to crack WEP.
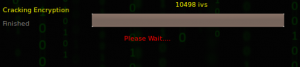
In my case, the Fern WiFi cracker didn’t succeed until it captured about 25,000 IVs.
But finally, if everything worked as it should, you’ll get the message below: